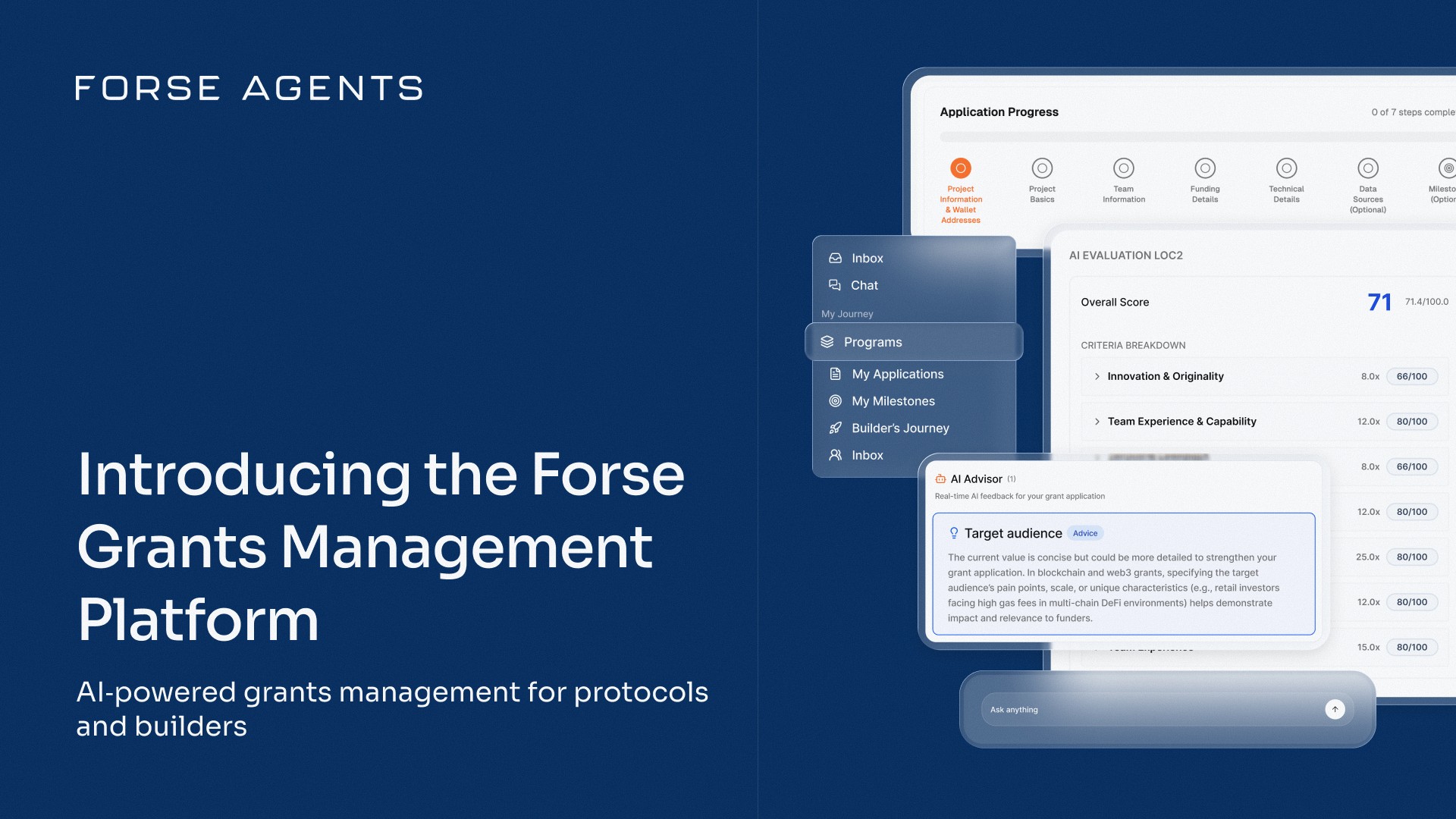
Decentralized Autonomous Organizations (DAOs) use token-weighted polling to make decisions. The security of this process hinges on how voting power is distributed. Two key metrics for assessing DAO governance security are the votable supply (the total number of delegated tokens) and the number of delegates required to pass quorum. Analyzing these factors provides insight into a DAO’s resilience against manipulation or centralization risks.
Votable Supply: The Foundation of Voting Power
Votable supply refers to the total number of tokens that have been delegated for governance participation. In many DAOs, token holders can either vote directly or delegate their tokens to representatives (delegates) who vote on their behalf. A higher percentage of delegated tokens typically indicates greater community engagement, but it also reveals potential vulnerabilities. For instance, if a small fraction of the total token supply is delegated—say, 10% of a 1 billion token supply (100 million tokens)—a well-funded attacker could acquire or influence enough tokens to sway decisions. Conversely, a widely delegated token supply (e.g., 70-80% of tokens) suggests broader participation, making it harder for any single entity to dominate.
To measure this, calculate the ratio of delegated tokens to the total token supply:
Votable Supply Ratio = Delegated Tokens / Total Token Supply
A low ratio may signal apathy or centralization (if only a few hold delegated power), while a high ratio reflects a healthier, more decentralized system.
Quorum and Delegate Thresholds: The Decision-Making Bar
Quorum is the minimum level of participation required to legitimize a governance decision, often expressed as a percentage of votable supply or a fixed number of votes. For example, a DAO might require 40% of the votable supply (e.g., 40 million tokens if 100 million are delegated) to approve a proposal. The number of delegates needed to reach this threshold further shapes security.
If quorum is low and concentrated among a handful of delegates—say, 5 delegates control 50% of the votable supply—a DAO becomes susceptible to collusion or bribery. To assess this risk:
Determine the quorum requirement (e.g., 40% of votable supply = 40 million tokens).
Count the minimum number of delegates needed to meet or exceed this threshold, based on their delegated token holdings.
Evaluate concentration: If fewer than 5-10 delegates can consistently pass quorum, the DAO’s governance is effectively oligarchic, undermining its decentralization.
Practical Example: Optimism Collective ($OP)
For a real-world example, we looked at Optimism Collective, the DAO in charge of many aspects of the Optimism Layer 2 Network.
Our Approach
The Target Votable Supply model emerged from a recognition that protocols needed a more sophisticated way to analyze governance security. Existing approaches typically focus on single metrics like quorum requirements or token distribution, without considering how these factors interact under different market conditions and attack scenarios.
Our model introduces several key innovations. First, it incorporates dynamic market conditions, including price slippage effects and lending market interactions. Second, it considers various levels of delegate’s willingness to collude, ranging from optimistic to pessimistic scenarios. Finally, it provides actionable targets for votable supply based on desired security thresholds.
The model analyzes multiple parameters including:
Market conditions (favorable, neutral, unfavorable)
Lending strategies (none, safe, aggressive)
Delegate collusion scenarios (1-3 delegates)
Price slippage effects
Token circulation and voting patterns
We've developed three primary scenarios - Pessimistic, Neutral, and Optimistic - each modeling different market conditions and attacker capabilities. This allows protocols to prepare for various threat levels and market environments.
Model Details and Methodology
The Target Votable Supply model operates through several interconnected modules, each analyzing specific aspects of governance security.
The Circulating Supply module projects token distribution over time, incorporating public $OP vesting schedules and unlock periods. This provides the foundation for understanding how many tokens could potentially be available to attackers and delegates alike.
The Votable Supply module analyzes historical voting patterns to estimate what percentage of circulating tokens might be available to participate in governance. This helps establish realistic baselines for attack scenarios.
The Lending Supply module projects potential lending market dynamics, crucial for understanding how attackers might leverage borrowed tokens. Even though lending markets may not currently exist for all governance tokens, this forward-looking analysis helps protocols prepare for future scenarios. In the case of $OP some limited lending capacity is available on Aave, for example, but nowhere near a meaningful amount for a governance attack.
The Price Slippage module uses the BARRA price impact formula to model how large token purchases affect market prices. This is particularly important for understanding the true cost of acquiring voting power through market purchases.
Finally, the Quorum module calculates both minimum and sufficient votable supply needed for proposal to pass under various scenarios.
Results for Optimism Collective
Our interactive terminal allows us to compare different scenarios by fine-tuning the parameters on the left and by selecting the level of collusion and the distribution targets that should be modeled.
This can lead to a visceral understanding of the sensitivity of governance security to these parameters.
Our terminal can be accessed here: https://dashboard.forse.io/main/optimism/votable_supply_framework

Environment Assumptions
Working from current observations about votable supply, we extrapolated the ratio of circulating to votable supply based on historical data. We found that the ratio tapers slightly off over time, unless specific measures to the contrary are taken. This tapering was used in our calculations.

Votable Supply Required to Prevent an Attack on Governance
We can clearly see that token emissions play as much of a role in the cost of attack as available lending depth. And that choosing and monitoring major delegates and even large whales is crucial for a truly informed real world picture of governance security.
It is impossible to be attack secure when certain whale addresses can unilaterally overcome any opposition. Tight monitoring is essential to security research.
Applications
The Target Votable Supply model provides valuable insights for multiple stakeholders in the ecosystem. Protocol designers can use it to set appropriate quorum requirements. Governance participants can better understand the security implications of their delegation decisions. Security teams can proactively identify potential vulnerabilities before they can be exploited.
The model's flexibility allows it to be adapted for different governance structures and token economics, making it valuable across various protocol designs.
Strengthening Governance Security
To enhance security, DAOs can:
Encourage broader delegation to increase votable supply.
Set higher quorum thresholds to prevent small groups from deciding outcomes.
Limit delegate concentration by capping individual voting power or incentivizing more delegate participation.
Monitor whale behaviour and do forensic research to identify these addresses.
Conclusion
Measuring DAO governance security through votable supply and delegate quorum dynamics offers a clear lens into its decentralization and resilience. A high votable supply ratio paired with a quorum requiring diverse delegate input signals a secure system, while low participation or concentrated power warns of potential exploits. By monitoring these metrics, DAOs can better safeguard their autonomy and align with their decentralized ethos.
Share with your friends: